2023-04-08|1 min read|[web]
inclusion
PHP filter abuse for LFI.
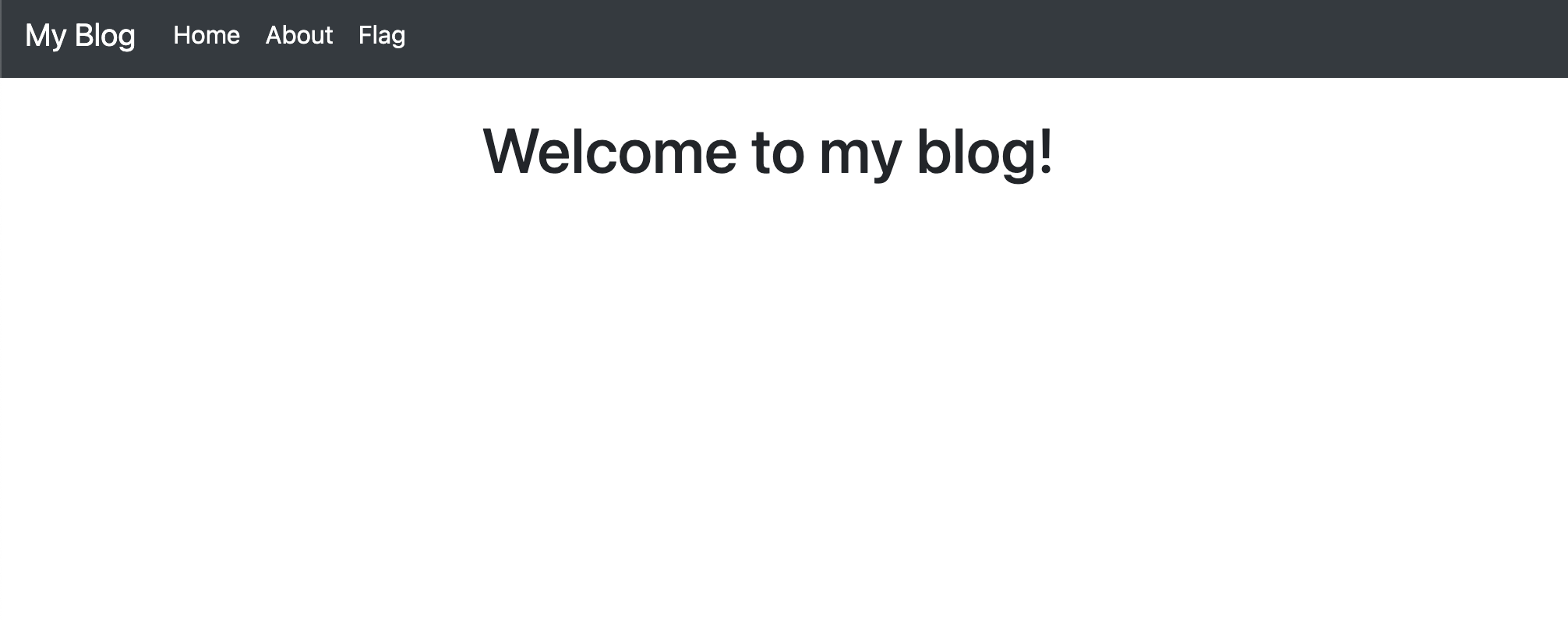
Upon starting, I noticed that the page was likely using include since pages were being rendered based on the page parameter. For example, /index.php?page=welcome provided the following:
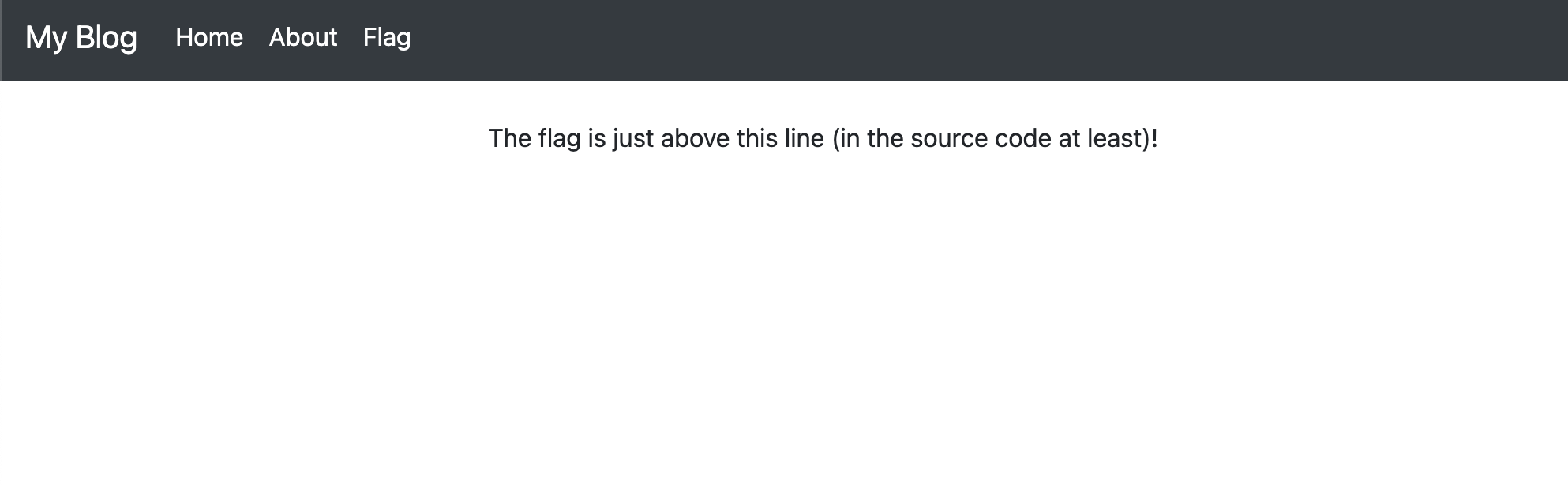
/index.php?page=flag would provide the following:
I decided to test this by rendering /flag.php and the following was shown:

However, the file extension was not added to the path parameter, which is likely due to a hard coded .php string being added to the parameter passed. This affected the way I exploited the LFI.
After referencing some online source, I used the following payload:
/index.php?page=php://filter/convert.base64-encode/resource=flag
Which yielded the following output:
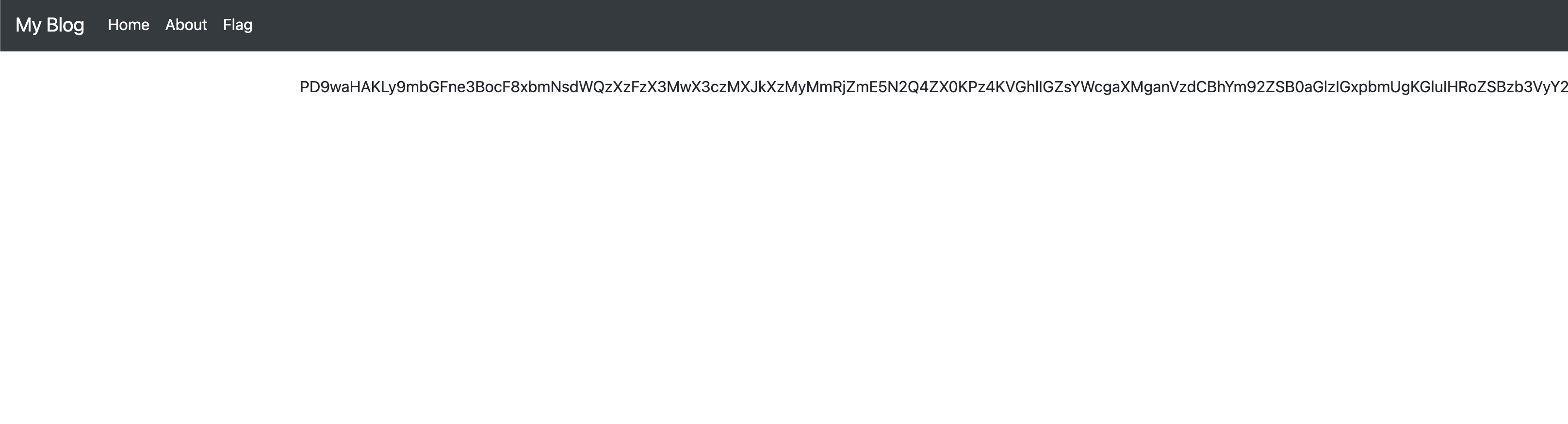
Once I base64 decoded the content, I saw the following php code:
<?php
//flag{php_1nclud3_1s_s0_w31rd_322dcfa97d8e}
?>
The flag is just above this line (in the source code at least)!