2023-04-09|1 min read|[rev]
postage
Speedy mail delivery.
Overview
Taking a quick look at the binary, it looks like we are prompted for an answer, which if incorrect, may lead to a segfault.
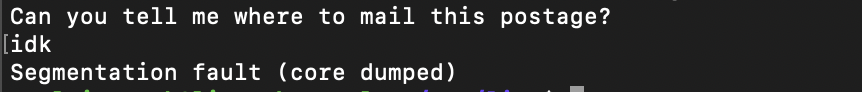
Lets take a closer look.
Reversing
After an initial review of the binary, this challenge looked very straight forward.
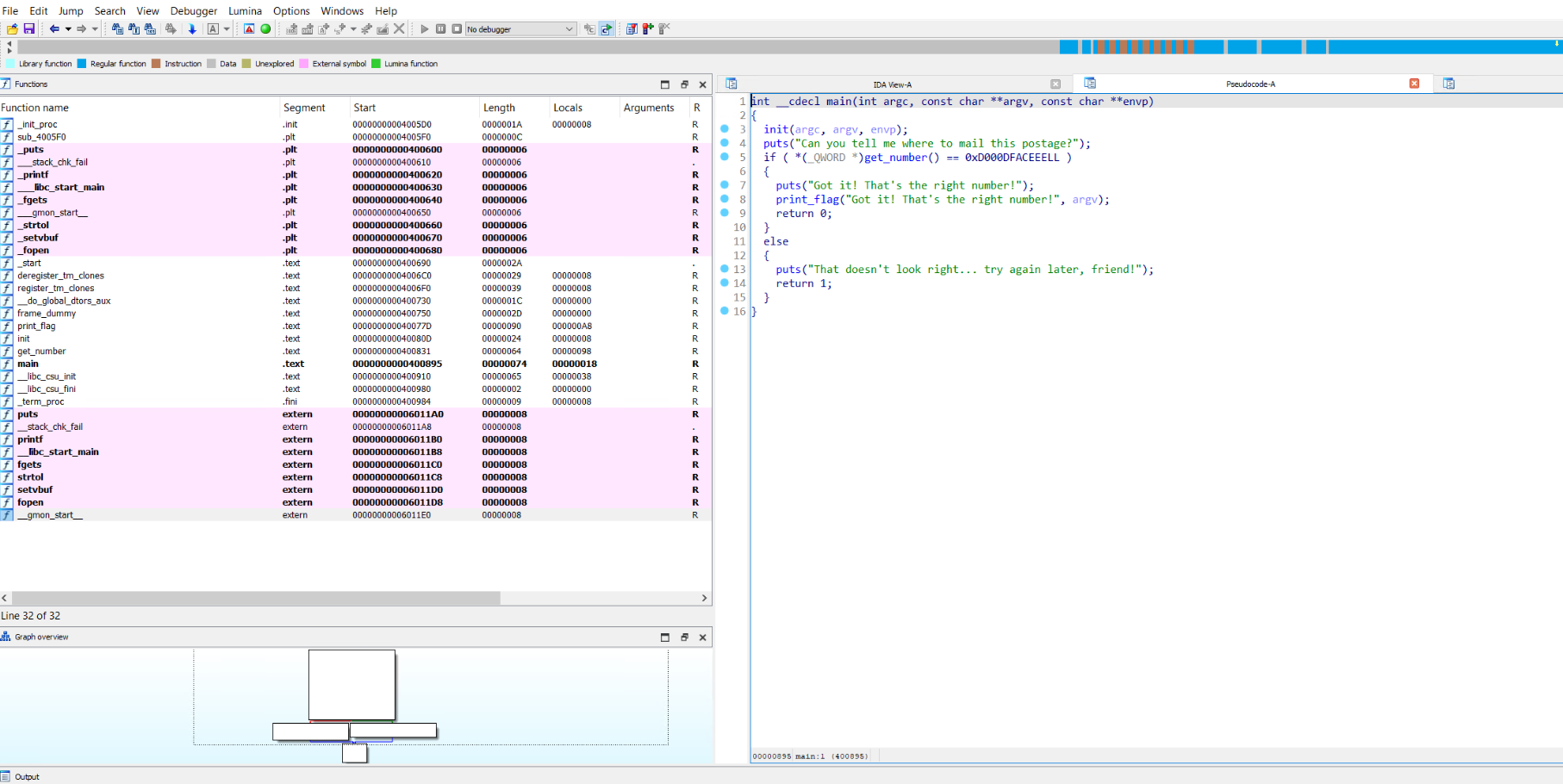
It wasn't until I took a closer look at the binary's dissassembly that I realized the value at the memory address supplied (returned from get_number) was actually being used to compare to 0x0D000DFACEEE :
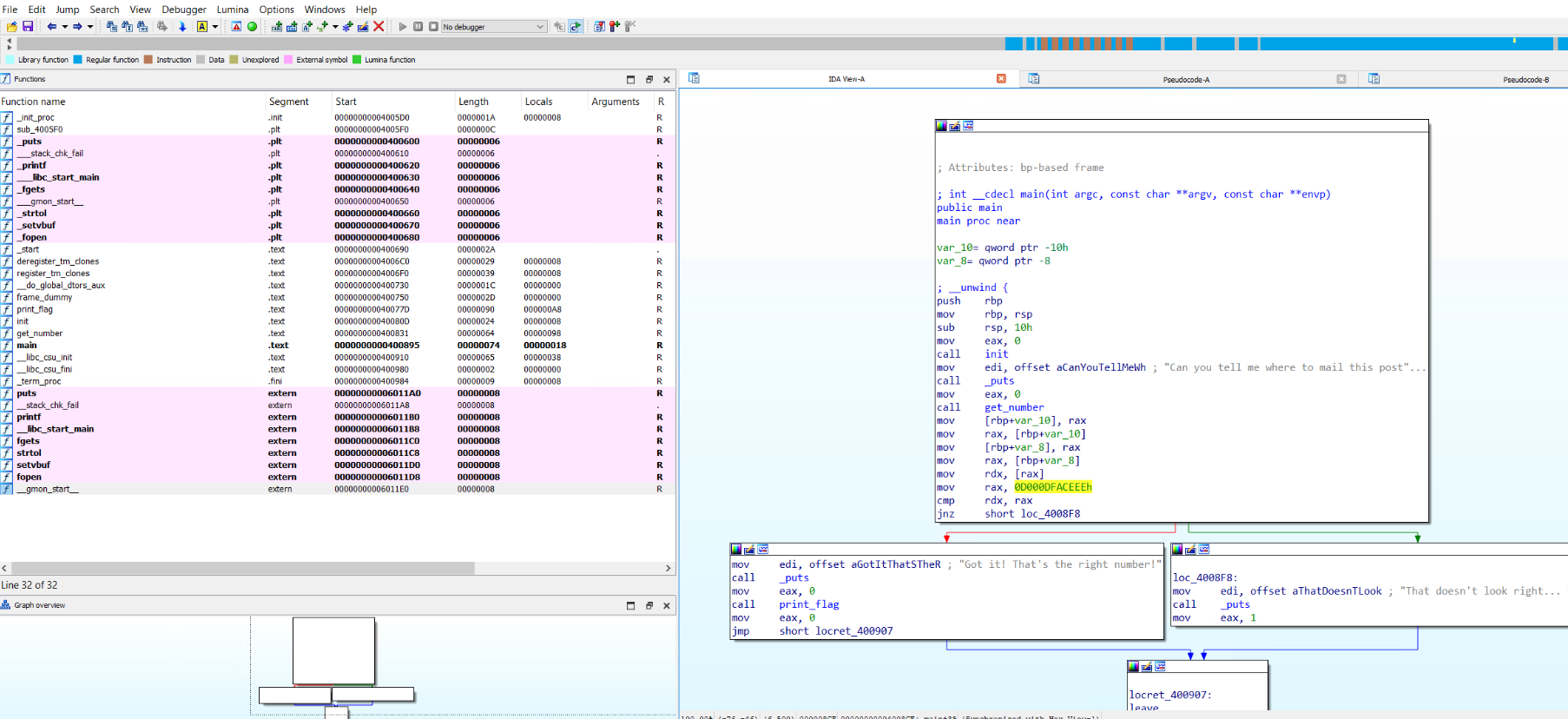
So instead of passing 0x0D000DFACEEE to solve, I searched for where in the binary data the value 0x0D000DFACEEE would be stored.
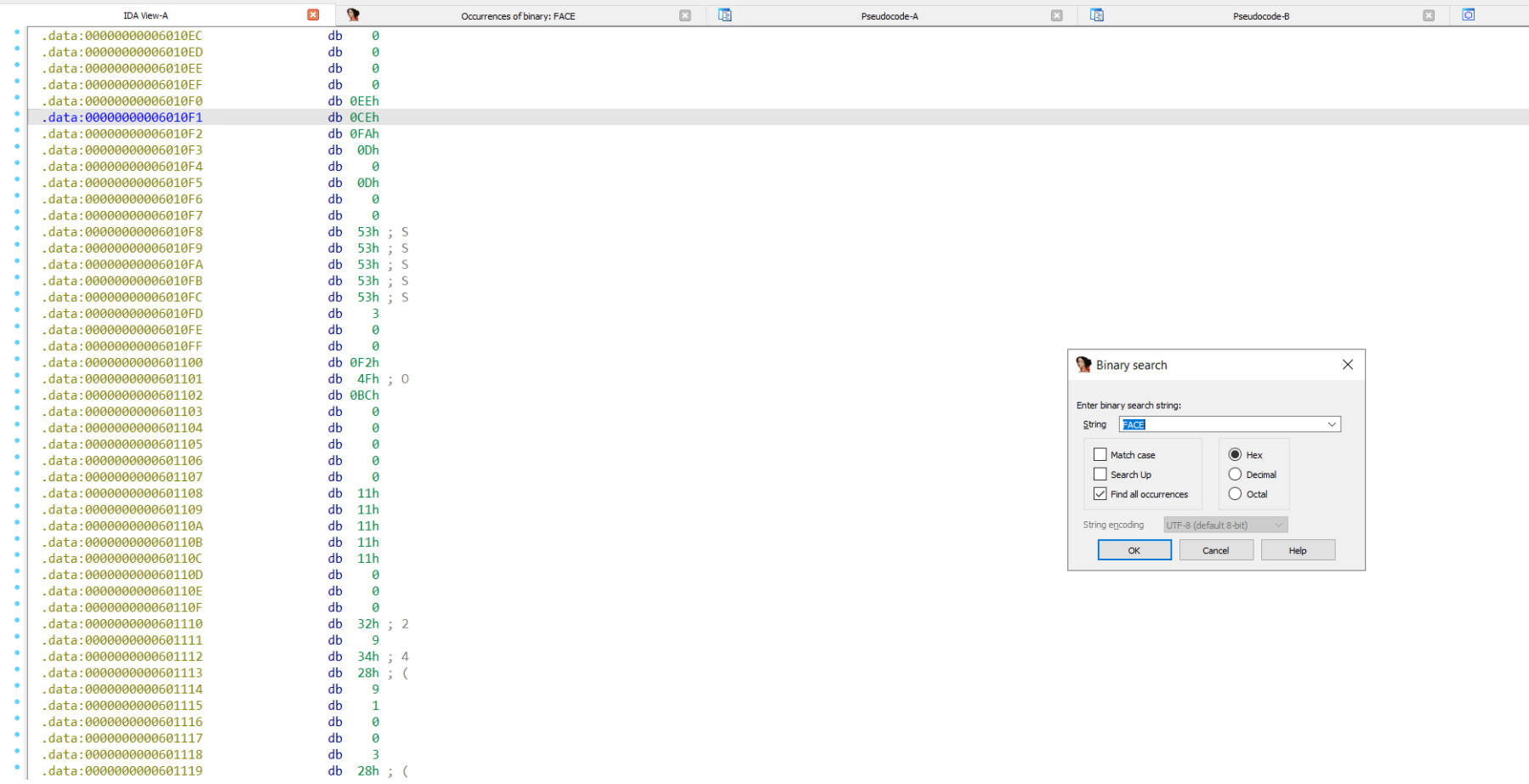
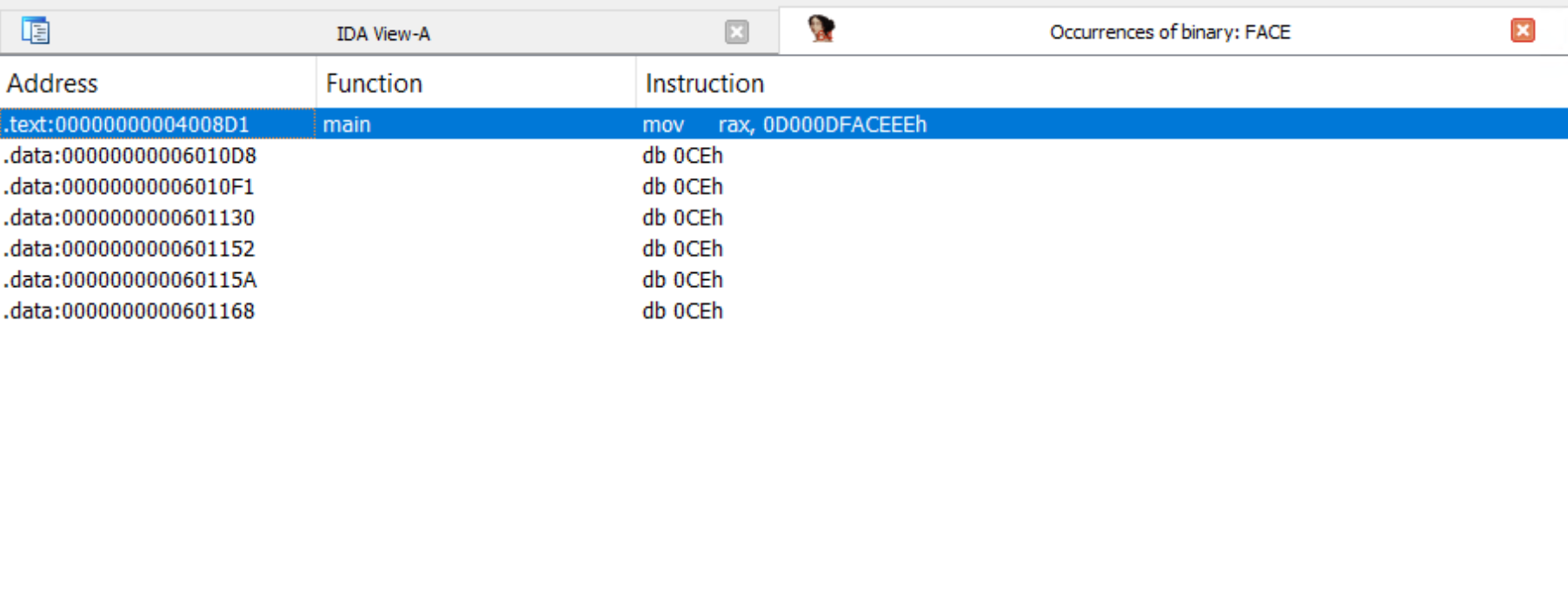
After finding the correct address of 0x6010F0 I was able to write my solver script to find the flag.
Solution
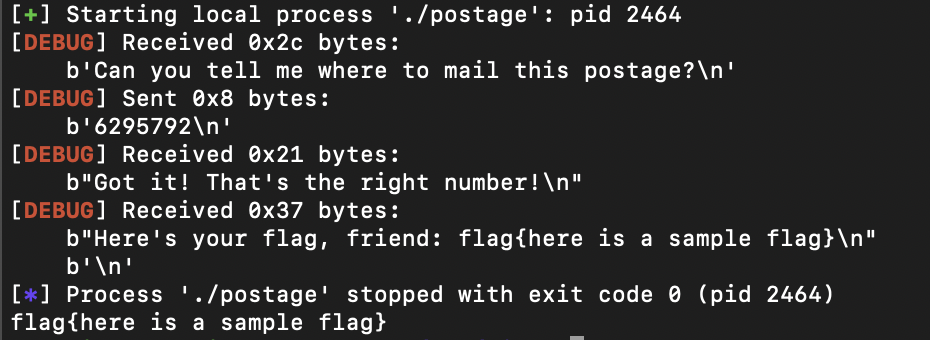
Solver
from pwn import *
from pwnlib.util.packing import *
# Context
context.arch = 'amd64'
context.log_level = 'DEBUG'
# Main vars
NETID = ''
HOST, PORT = 'host', 1247
def pwn():
conn = remote(HOST, PORT)
conn.recvuntil(b'(something like abc123): ')
conn.sendline(NETID)
conn.recvuntil(b'Can you tell me where to mail this postage?\n')
x = str(0x00000000006010F0).encode('utf-8')
conn.sendline(x)
conn.recvuntil(b'flag{')
response = conn.recvline()
conn.close()
print("flag{" + response.decode().strip())
if __name__ == "__main__":
pwn()